How the Internet Works, Part I - The Internet Infrastructure
Understanding The Main Components of The Internet
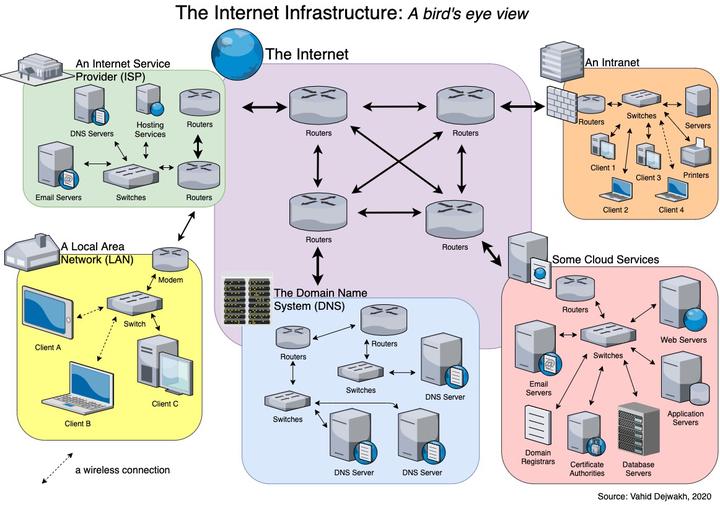
ISPs, routers, gateways, LANs, HTTP, the cloud, the web… the Internet is so complex that we could spend days, months, and even years studying this stuff, and we still wouldn’t be done.
But just several minutes is all we need to at least get the basics down.
Let’s first understand the main components of the Internet–the infrastructure that supports the entire web. Here we’ll review what routers, modems, gateways and switches are, the difference between a web server and an an application server, and some esoteric things like the Domain Name System (DNS) and domain registrars.
Building this mental model of the Internet’s infrastructure will then allow us to get deeper into the layers of the OSI and the TCP/IP models, which we’ll cover in Part II. These layers will help us understand every step that occurs from the time we enter a URL in our browser to the time we get a fully functioning webpage displayed.
Finally, in Part III, we’ll go even deeper into each layer’s contents, and thereby explore how security works.
In the process, we’ll develop a better appreciation for the complexity and brilliance of this thing we’ve all come to love–and maybe also sometimes hate?
I. The Internet Infrastructure: A bird’s eye view
- 1. Local Area Networks (LAN)
- 2. Internet Service Providers (ISP)
- 3. The Domain Name System (DNS)
- 4. Cloud Services
- 5. The Internet
- 6. Intranets
- PDF of the Internet Infrastructure diagram
1. Local Area Networks (LAN)
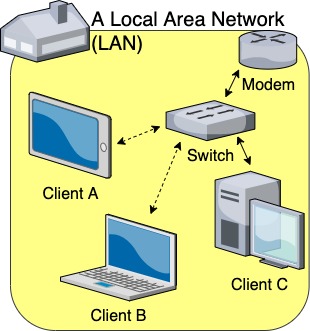
At the most basic level, we are all familiar with our home’s Local Area Network, or LAN. That’s how most of us working from home (or surfing the web from home) connect to the Internet.
Our home’s LAN allows multiple devices, or clients, to connect either via an Ethernet cable or wirelessly to a switch (what most of us colloquially call a “router”), which is itself connected to a modem.
Sometimes we may have a gateway instead of those two separate units, which is a single unit that combines the responsibilities and capabilities of both a modem and a switch.
Key terms:
-
MAC Address & NIC Cards: each device that can connect to a network does so through its Network Interface Card (NIC). Each NIC has a unique Media Access Control (MAC) address, which is a physical, hardcoded identifier that distinguishes that device on a network. To ensure that devices from different manufacturers don’t accidentally get assigned the same MAC address, the Institute of Electrical and Electronics Engineers (IEEE) assigns each NIC manufacturer the first 24 bits of the MAC Address that all their devices must contain.
-
IP Address: each device on a network can be statically or dynamically assigned an IP address by a switch, through the DHCP protocol. Unlike a MAC address, an IP Address is not hardcoded into a device, but is instead logical and hierarchical, which allows a device to be more easily located based on its IP address.
-
Switch: a networking device that sends data to the appropriate device within the LAN, using an ARP table that matches each IP address to a MAC address.
Note: In layman’s terms, this is often referred to as a router, but here we’ll reserve the term router to describe a more specific and capable type of switch that can bridge traffic between two networks. More on this in the next section below. -
Modem: a device that serves as a bridge between a LAN and a WAN (wide area network). A LAN that is connected to the Internet does so through its modem (or Gateway). Devices on a LAN could still communicate with each other without a modem, but they just wouldn’t be able to access the Internet.
-
Gateway: The combination of both a switch and a modem.
-
Ethernet: The protocol that allows for communication within a LAN.
-
802.11: The protocol that allows for wireless communication (i.e. wifi) within a WLAN (wireless local area network). Designations (such as a, b, c, g, h, n, ac, or ax) further distinguish the wireless speeds and frequencies at which devices with that protocol compatibility can operate.
2. Internet Service Providers (ISP)
Our LAN connects to an ISP’s infrastructure via our modem (or Gateway). We usually pay our ISP a monthly fee for this service, which ultimately allows us to connect to the wider Internet.
In the United States, some of the biggest ISPs include AT&T, Cox, Comcast, and Verizon.
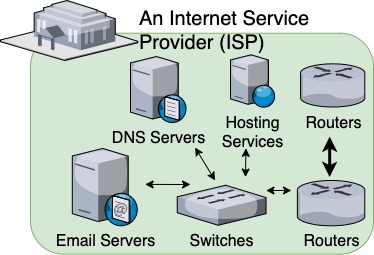
ISPs typically offer plans with different connection speeds, which establish different bandwidth levels for the customer, with the higher bandwidth plans costing more.
Most plans provide broadband-level connectivity, whether through a coaxial cable or fiberoptic connection. Some ISPs still offer the slower DSL connections, but at least the dial-up days are no more.
Through a series of routers, our ISP’s infrastructure directs traffic between the many households it serves and the wider Internet. Traveling through all these hops across many routers means there’s always going to be some latency in our connection, regardless of our connection’s bandwidth.
ISPs may provide their customers with email addresses. Someone with a @cox.com or @aol.com email address, for example, has probably gotten it from their ISP (Yes, AOL used to be an ISP back in the day). Email services would be handled by the ISP’s email servers, through an SMTP protocol.
ISPs may also provide some basic hosting services to handle their customers' personal websites, which would run on the ISP’s web servers. More on web servers in the Cloud Services section below.
Lastly, ISPs also provide DNS servers. We’ll address what these do in the DNS section (next), but suffice it to say that they offer cached copies of what the main DNS provides, in order to expedite the process of retrieving data from the Internet.
Key terms:
-
Bandwidth: The amount of data that can be sent during a specific unit of time (typically a second) across a network. We can think of the number of lanes on a highway as being analogous to the concept of bandwidth.
-
Broadband: According to the Federal Communications Commission (FCC), an ISP must deliver at least 25 Megabits per second (Mbps) download speeds and at least 3 Mbps upload speeds to qualify as broadband.
-
Mbps v.s. MBps: A byte is equal to 8 bits. MBps refers to megabytes per second, and Mbps refers to megabits per second. It is a brilliant marketing move by ISPs to describe their plan speeds in terms of Mbps instead of MBps, because most customers don’t know the difference between a bit and a byte–and therefore think they’re getting more bandwidth than they actually are.
A customer might erroneously assume that a 10 Mbps connection means that it would take one second to download a 10 MB file, but that would actually require an 80 Mbps connection. Now you are among the proud, the few that know the difference. You’re welcome. -
Download speed: The bandwidth size of the traffic coming from the Internet (i.e. an external server) to the client.
-
Upload speed: The bandwidth size of the traffic going from the client to an external server on the Internet.
-
Router: a switch that can also send data across networks (i.e. from one network to other networks). Because IP addresses are hierarchical, a router knows which secondary router it’s directly connected to would be better able to either find the correct network containing the device with that IP address, or at least get it one hop closer to that network.
-
Latency: The time it takes for one piece of data to go from point A to point B in a network. Whereas bandwidth measures the maximum size of data per a set unit of time (i.e. a second), latency measures the time it takes for a set, minimal size of data.
To use our highway analogy, a single car traveling at the same speed limit across the same geographic span would take the same amount of time, no matter if you increased or decreased the number of lanes on the highway. The only situation where increasing bandwidth might make a difference in the latency is when there’s so much traffic that data is stuck in a bandwidth bottleneck somewhere. -
Last-mile latency: The latency specific to the last link stretch closest to the customer, a stretch often called the “last mile.” This last-mile latency is what ISPs tend to focus on, since that’s the main segment they have control over. We’ll look at the different types and sources of latency in the Internet section (Section 5).
3. The Domain Name System (DNS)
Whenever you use your browser to go to a specific website (e.g. https://vahid.blog), your browser application needs to first figure out which server would have the correct website information.
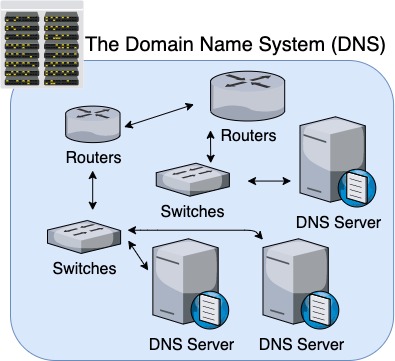
After all, a domain name (e.g. vahid.blog) doesn’t tell us anything about the IP address of the server containing the website we’re looking for.
That’s where the Domain Name System (DNS) comes into play.
Every time you go to a website you’ve never been to before, your browser has to first triangulate the IP address associated with that domain.
It first hits up the DNS Servers supported by your ISP. If those servers don’t have a record of that domain either, they then forward the request further up the chain until it gets to the DNS, when the request travels down the DNS hierarchy from the root name servers down, until it finds the IP address of that domain name.
Your browser will then cache (i.e. save) that domain-to-IP address key-value pair so that it won’t have to look it up again the next time you enter that domain.
Why do we need this process? It’s simply for convenience, because it’s much easier to remember, for example, “google.com” than it is to remember an IP address.
You could of course enter the IP address directly into your address bar instead. For where I live, my ISP’s DNS Servers send me to 172.217.15.100 whenever I go to google.com. So I could enter 172.217.15.100 directly in my browser, too. Unless I’m Rain Man, I probably wouldn’t do that regularly.
Depending on where you live, and because Google is such a ginormous application requiring thousands of servers spread out across the globe, you may be sent to another server closer to you, with another IP address.
Key terms:
-
domain name: A domain name is a unique identifier that points to an IP address, or several IP addresses. A domain name consists of a combination of at least two parts: a top-level domain (TLD) to the right of the (rightmost) dot, and a second-level domain (SLD) to the left of the (rightmost) dot.
For the domain “google.com” for example, com is the TLD and google is the SLD. Other common TLDs include net, org, edu, gov, co, and country codes like uk, fr, ca, etc.
Some domain names may also contain an optional, third-level domain (called a subdomain), which would further delineate and carve out a unique IP address pointing to a different server. Some common subdomains include: www, which is often the default subdomain for a home page, blog, which delineates the organization’s blog, and ftp, which points to a server that handles file uploads–but anything could be a subdomain.
You could have domains that have fourth, fifth, and even sixth level domains, and theoretically could keep going even beyond that.
The key concept to keep in mind is that the domain keeps getting more and more specific as you go from right to left, each level being separated by a dot. -
ICANN: The Internet Corporation for Assigned Names and Numbers (ICANN) is the international organization in charge of maintaining the DNS root zone (among many other things). You may have noticed that new TLDs (like .dev or .io) keep popping up, especially as the .com TLD gets more saturated and used up. The Internet Assigned Numbers Authority (IANA), a department of ICANN, oversees that entire process.
-
Registry Operators: Usually, a company or organization might purchase the rights to a TLD from ICANN through a strenuous and expensive application process. If they are successful, they can then become registry operators, and start selling yearly licenses to other third parties who want to carve out an SLD for themselves from (and with) that TLD.
Registry Operators (like VeriSign, the owner of the .com and .net TLDs) used to sell SLDs directly to customers. Now, however, they typically act more like wholesalers who rely on Domain Name Registrars like GoDaddy or PorkBun to be their retailers. Registrars have to be accredited, and typically bump up the price in order to earn a profit.
IANA keeps a list of all the TLDs and their Registry Operators here:
The Root Zone Database. There were over 1500 TLDs at the time of the publication of this post, i.e. December 2020. -
DNS Servers: When we say that the DNS is hierarchical in nature, we mean that there are logical steps for identifying the IP address of a particular domain name. This hierarchical process is handled by various levels of DNS Servers, routed and structured by domain name level.
For example, when looking up the IP address of the William & Mary Law School’s domain name, law.wm.edu, the first step in the DNS lookup process would be to find the DNS Servers that handle the .edu TLD. Once we’re at that branch of the tree, we can then look up the DNS Servers that handle the wm SLD. Finally, once we’re at that secondary branch, we can then more specifically look up the law subdomain.
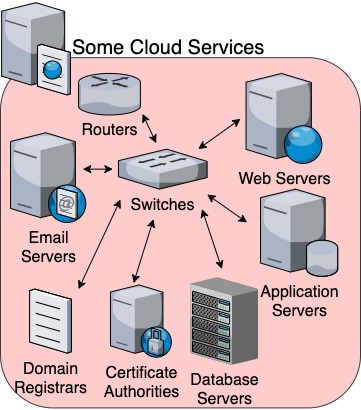
4. Cloud Services
Wow, that was a long–but important–detour.
The next step in our journey is understanding the various types of cloud services that companies on the Internet provide–services that are crucial to our ability to do everything from sending emails to shopping securely.
For software engineers and web developers, cloud services also enable us to smoothly and quickly build database-driven applications, with increasing complexity and compartmentalization capabilities.
A general concept to keep in mind as we discuss some of the various types of services that fall under this category is that these services are not necessarily independent silos, nor are they necessarily bundled together.
Companies may only provide one type of service, or many. Some may specialize in one type and then outsource other services to other companies, or just make sure their service is interoperable and compatible with other types of services from other companies. This interoperability is often accomplished through APIs.
A secondary concept is that companies typically have hundreds, thousands, and maybe even millions of servers, sometimes distributed all over the globe–and they keep adding more as demand for their services grows. For example, Google had an estimated 900K servers in 2011. Gartner estimated that by July 2016, this number had grown to 2.5 million.
Key terms:
-
API: An Application Programming Interface (API) allows interaction between two different systems, including systems operated by two different companies. This can be accomplished either through a backend interface hidden from the user and generally designed specifically for developers, or through a frontend interface that is more user-friendly.
-
Email Servers: Although there was a time when your options for email addresses were limited either to what your ISP or your company offered, you can now easily get all sorts of free email addresses, from Gmail to Outlook to Protonmail and Idontknowwhatelsemail. These are offered by companies or organizations that either have their own email servers or pay for access to third-party email servers.
-
Web Servers: Servers that host static content (including HTML, Javascript, and CSS files) are called web servers. These are sites that don’t require much backend processing power, and can merely deliver prepackaged content without having to handle business logic. Most landing pages, basic company websites, news sites, personal pages, and blogs, such as this one, are hosted by a web server. Web servers probably account for the largest chunk of all server types.
-
Application Servers: Although a personal blog might be hosted by a basic web server that can easily deliver read-only content, there might be an underlying application (e.g. Wordpress) that needs to not just read, but also actually generate, edit, and delete new static content.
Application Servers require much more processing power than web servers because they need to be able to handle the more elaborate, business-logic requests coming from millions (or billions) of users.
A ubiquitous application like Facebook would still require many many dedicated application servers, also distributed across the globe, but sometimes one application server can host several small-scale application prototypes. -
Database Servers: Often used in collaboration with application servers (but can also be independent), database servers (also called data stores) are designed to manage databases. There are two main types of database structures used in database design: either a relational model (usually SQL), or a non-relational model (usually the document model). PostgreSQL is an awesome relational database provider, and MongoDB is an excellent choice for a non-relational database provider.
-
Domain Registrars: We already briefly mentioned these in section 3, but it’s worth discussing them again in more depth, and in the context of a cloud service. Domain Registrars allow you to register your own domain name, for a yearly fee, so that you can direct traffic to that domain name to whatever server, with whatever IP address, you choose. Some registrars also provide basic hosting services, and occasionally have promotional deals where you can register a domain for free (for a year) if you purchase hosting services from them.
-
Certificate Authorities: Lastly, we should briefly mention Certificate Authorities (CA), which have evolved and grown out of the increasing need for better security. These companies, also organized in a hierarchy, provide digital certificates that ensure content is coming from a trusted source. We’ll get deeper into CAs in Part III, where we’ll discuss how security protocols like TLS and HTTPS work.
5. The Internet
The Internet connects ISPs, the DNS, and Cloud Services together, and allows them to communicate. This is of course a simplification, and network engineers spend years and decades getting deeper into the weeds.
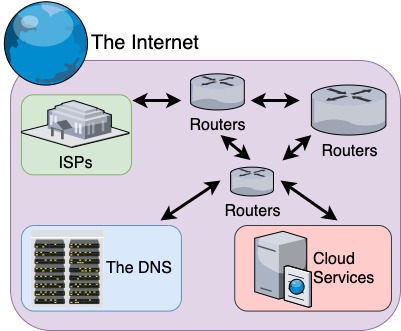
But for our purposes, it’s useful to think of the Internet as just a network of routers spanning across the entire world, connecting networks together.
Each router redirects data across a hop to another router, getting the data progressively closer to its final destination IP address.
Along the way, a signal will encounter four different types of latency, causing a delay to its arrival time:
-
propagation delay: The natural limits of a signal traveling from sender to receiver, which can be calculated as the ratio between distance and speed, with speed usually being the speed of light. We can think of propagation delay as the physical limits imposed by nature and geographic distance.
-
transmission delay: The delay that occurs as a result of the signal traveling down multiple hops or links, interconnected by routers and switches, etc. Reducing the number of hops required would thereby reduce the transmission delay.
-
processing delay: The delay incurred by having to process data at any point along the transmission route. We could potentially reduce processing delay by upgrading to more efficient routers that can redirect traffic faster.
-
queuing delay: The delay that occurs when the data is in line waiting to be processed. This can be caused either because of insufficient bandwidth, a particularly high traffic time of the day, or an inefficient router. If data is arriving at a router at a faster rate than the router is able to redirect it appropriately, this gives rise to queuing delay. Breaking up a hop into several hops, with more routers, may help to reduce queuing delay, but it may add to transmission delay.
Key terms:
-
TCP/IP protocol suite: A protocol is a set of rules that governs how communication is handled. The TCP/IP protocol suite, also known as the Internet protocol suite or the Department of Defense (DoD) model, is the set of protocols that has become dominant across the globe. Part II of this series explores the five layers of this model, compared against the seven layers of the OSI Model.
-
routing table: A router keeps track of all the IP addresses of the devices on its network, including of course other routers. This routing table allows the router to determine which router to send data to in order to get it closer to its destination.
-
RTT: Round-trip time. Essentially the sum of the latency of going from A to B, plus the latency of coming back from B to A.
6. Intranets
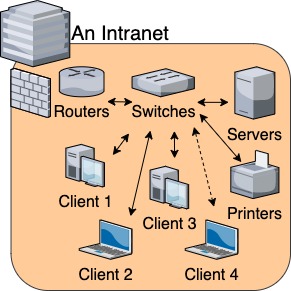
Our last topic is on Intranets, which are also called private networks.
Although not technically part of the Internet, and separated from the Internet by a firewall for added security, an intranet is nevertheless an important concept to understand and place within this overall structure.
Most organizations have their own individual servers, routers, and switches that connect all computers and devices in the organization together, which allows all employees to access shared drives, printers, and common applications like HRIS and financial systems.
An intranet also allows a user to log in to any computer on the network, and access their personal network drive.
Depending on the size of the organization (and how many computers and servers need to be connected), an intranet could be anywhere between just a slightly more extensive LAN, or a mini-internet that spans across many countries.
Key terms:
- VPN: A virtual private network (VPN) allows someone with the right login credentials to access their intranet from outside the intranet, through the Internet (rapidly repeat that five times in a row!). A VPN essentially establishes a secure line to the intranet’s network, making it seem like the client is on the organization’s premises, connected directly to the intranet.
That’s it for Part I!
In Part II of this three-part series, we’ll dive deeper into the seven layers of the OSI Model and the five layers of the TCP/IP model.
In the process, we’ll also explore what happens at each layer from the moment we enter a URL in our browser to the time we get a page loaded.